Enquiry Form
What is Access Control System Software?
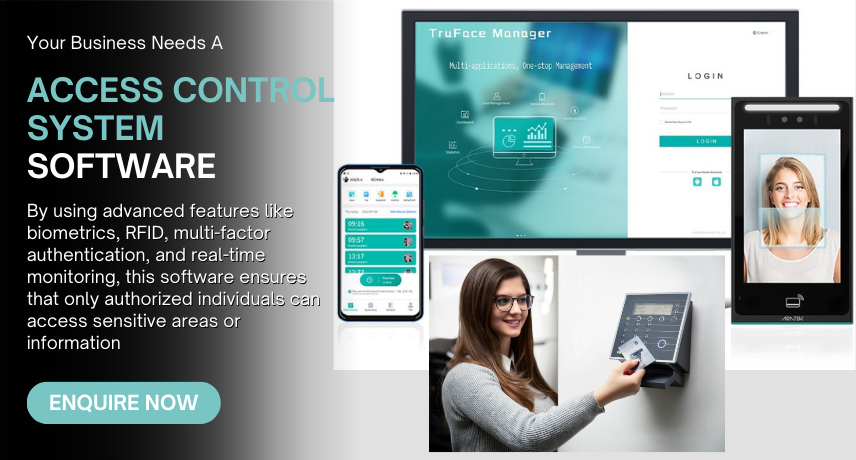
Access Control System Software is a security solution designed to regulate and monitor access to physical or digital resources within an organization. By using advanced features like biometrics, RFID, multi-factor authentication, and real-time monitoring, this software ensures that only authorized individuals can access sensitive areas or information. It plays a crucial role in enhancing security, ensuring compliance, and streamlining access management across various industries.
Best Features of Access Control System Software

Multi-Factor Authentication (MFA):
Combine passwords, biometrics, and hardware tokens for enhanced security.

Role-Based Access Control (RBAC):
Assign permissions based on user roles within the organization.

Real-Time Monitoring:
Track access events and generate instant alerts for unauthorized attempts.

Biometric Authentication:
Use fingerprint, facial recognition, or iris scanning for secure access.

RFID and Smart Card Integration:
Provide contactless access through RFID-enabled badges or smart cards.

Cloud-Based Management:
Manage access control remotely through cloud-based platforms.
Visitor Management:
Track and control access for visitors and temporary users.

Audit Trails and Reporting:
Maintain detailed logs of access events for compliance and analysis.

Mobile Access:
Enable employees to use their smartphones as access credentials.

Integration with Security Systems:
Sync with surveillance cameras, alarms, and other security systems.

Custom Access Schedules:
Define time-based access permissions for specific areas.

Emergency Lockdown:
Instantly secure all access points during emergencies.

Scalability:
Expand the system as the organization grows.

Data Encryption:
Protect sensitive access data with robust encryption protocols.

Access Request Automation:
Automate access approval workflows for efficiency.
Benefits of Access Control System Software
- Enhanced Security: Prevents unauthorized access and ensures only approved personnel can enter restricted areas.
- Centralized Control: Manages multiple entry points from a single dashboard, improving security oversight.
- Improved Employee Safety: Restricts access to high-risk zones and emergency exits for better workplace safety.
- Audit & Compliance Tracking: Keeps logs of access history, helping with regulatory compliance and security audits.
- Seamless Integration: Works with CCTV, alarm systems, HR management, and IoT security devices.
- Remote Access Management: Allows admins to grant or revoke access from anywhere using cloud-based control.
- Reduced Costs & Manual Effort: Eliminates the need for physical keys, reducing security staff workload and duplication risks.
- Customizable Access Levels: Assigns role-based permissions to employees, contractors, and visitors.
- Real-Time Alerts & Monitoring: Sends instant notifications for unauthorized access or security breaches.
- Scalability for Business Growth: Expands as needed to accommodate new locations, employees, or security requirements.
Which Businesses Need Access Control System Software?

Businesses implement access control systems to enhance security and manage employee access.
- Secure Entry Management: Restrict unauthorized access to sensitive areas.
- Multi-Factor Authentication: Combine biometrics, RFID, or PIN codes for higher security.
- Visitor Management: Track and manage guest access efficiently.
- Employee Attendance Tracking: Automate work-hour logging with access credentials.
- Remote Access Control: Allow administrators to manage access settings remotely.
- Incident Reporting: Log access attempts and generate security reports.

Hospitals and clinics use access control to protect patients and sensitive data.
- Restricted Area Access: Limit entry to labs, ICUs, and medical record rooms.
- Biometric Authentication: Ensure only authorized personnel access critical areas.
- Patient Data Protection: Secure electronic health records from unauthorized access.
- Emergency Lockdown: Enable quick lockdown during security threats.
- Staff & Visitor Tracking: Monitor movement within the facility.
- Integration with Surveillance: Link access logs with CCTV footage for security audits.

Schools and universities use access control systems for campus security.
- Campus Entry Restriction: Limit access to students, faculty, and authorized personnel.
- Smart ID Cards: Use RFID or biometric-based student identification.
- Library & Lab Access: Restrict and monitor access to specialized facilities.
- Time-Based Access Control: Allow entry only during specific hours.
- Dormitory Security: Manage and secure student housing access.
- Emergency Evacuation Assistance: Guide students and staff during emergencies.

Retailers deploy access control to secure premises and manage personnel.
- Stockroom Security: Prevent unauthorized access to inventory storage.
- Employee Access Levels: Grant different permissions based on roles.
- Customer Flow Control: Restrict entry to VIP or member-only areas.
- Theft Prevention: Integrate access logs with security systems.
- Automated Store Locking: Enable scheduled opening and closing of doors.
- Integration with POS Systems: Secure transactions by linking access with sales terminals.

Factories and warehouses use access control for safety and inventory protection.
- Zone-Based Access: Restrict entry to hazardous or high-value zones.
- Machinery Access Control: Allow only trained personnel to operate equipment.
- Supply Chain Security: Monitor access to storage and shipment areas.
- Employee Workshift Tracking: Automate attendance and shift logs.
- Fire & Hazard Safety: Implement emergency exit control systems.
- IoT & Smart Locks Integration: Manage access remotely through cloud-based control.
How to Choose the Best Access Control System Softwarer
Here Are The Best Ways To Choose the Best Access Control System Softwarer

- Security Features: Look for multifactor authentication, biometric access, and real-time monitoring.
- Scalability: Ensure the system can grow with your business and support multiple locations.
- Integration: Check compatibility with existing security systems, HR software, and IoT devices.
- User Management: Role-based access control and easy employee onboarding/offboarding.
- Remote Access: Cloud-based or mobile control for managing access from anywhere.
- Compliance & Data Security: Meets industry regulations like GDPR, HIPAA, or ISO standards.
- Cost & Support: Compare pricing, licensing models, and availability of 24/7 customer support.
Access Control System Software for Secure & Smarter Premises
Ensure safety with powerful Access Control System Software by Softwares In Demand. Monitor, manage, and restrict access with real-time control and secure authorization.